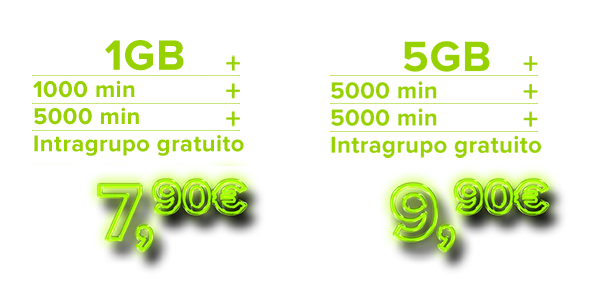
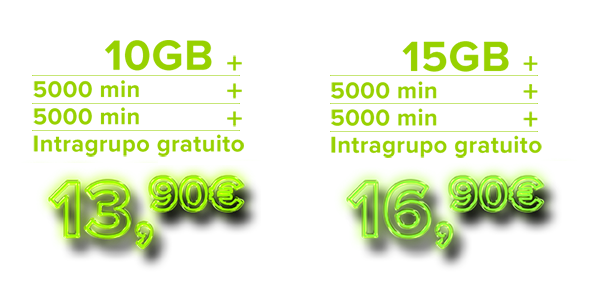
Oportunidades Móveis
Internet Empresarial
PORQUÊ ESPERAR PELO 5G SE PODE TER 10G?
A internet do futuro chegou.
Faça a sua empresa mais rápida, faça ONI.

Customizadas
FAÇA À
SUA MEDIDA,
SUA MEDIDA,
FAÇA ONI
Desenhamos consigo uma solução global personalizada, com a qual pode seguir o caminho da digitalização de uma forma simples e eficaz.
Cloud
FAÇA NA CLOUD,
FAÇA ONI
Com as nossas soluções personalizadas, criamos um ambiente simples e intuitivo para desenvolver todas as ferramentas digitais de que a sua empresa precisa.
Cibersegurança
FAÇA SEGURO,
FAÇA ONI
Tratamos das suas informações privadas com soluções de segurança de alto nível para proteger, em todos os momentos, a integridade dos dados da sua empresa.
Conectividade
FAÇA MAIS PELO SEU NEGÓCIO,
FAÇA ONI
Estamos sempre junto a si, a apoiar na digitalização da sua empresa para que ela continue a crescer. Conte com a ajuda de especialistas sempre que precisar e com um serviço pensado à sua medida.